|
VIRUS WARNINGS - Tips and Tricks |
|
| For the latest Virus Updates from Trend Micro, CLICK HERE. | |
One of world's top 10 spammers held in Seattle Robert Alan Soloway is accused of using networks of compromised “zombie” computers to send out millions upon millions of spam e-mails. “He’s one of the top 10 spammers in the world,” said Tim Cranton, a Microsoft Corp. lawyer who is senior director of the company’s Worldwide Internet Safety Programs. “He’s a huge problem for our customers. This is a very good day.” |
|
Latest Threat!W32.Mumawow!genRisk Level 1: Very LowDiscovered: May 30, 2007 Updated: May 30, 2007 10:20:27 AM Type: Worm Systems Affected: Windows 2000, Windows 95, Windows 98, Windows Me, Windows NT, Windows Server 2003, Windows XP W32.Mumawow!gen is a generic detection for the files infected by the W32.Mumawow family of worms.Files that are detected as W32.Mumawow!gen may be malicious. We suggest that you submit to Symantec Security Response any files that are detected as W32.Mumawow!gen. For instructions on how to do this using Scan and Deliver, read How to submit a file to Symantec Security Response using Scan and Deliver . RecommendationsSymantec Security Response encourages all users and administrators to adhere to the following basic security "best practices":
|
|
Latest Threat! SpyLockedUpdated: May 31, 2007 7:16:13 PM Type: Other Risk Impact: Medium Systems Affected: Windows 2000, Windows 95, Windows 98, Windows Me, Windows NT, Windows Server 2003, Windows XP BehaviorSpyLocked is a security risk that may give exaggerated reports of threats on the computer. The program then prompts the user to purchase a registered version of the software in order to remove the reported threats.Note: Definitions before May 18, 2007 may detect this security risk as VirusBurst. Protection
Click here for a more detailed description of Rapid Release and Daily Certified virus definitions. |
|
|
The first quarter saw more worms top the charts with WORM_NYXEM.E, a mass-mailing, network-propagating worm powered by an adult-themed social engineering scheme, continuing to lead the list. Worms of old, such as NETSKY and BAGLE, still prevail due to the amount of users who do not update their security software or lack it altogether.
While social engineering in the outbreak era used the blind hit-and-miss method, today's carefully planned, sequential attacks tailor their schemes to the targeted segment and are deployed where and when recipients may actually be misled. For the full story on this threat and more on spyware and virus threats visit the Trend Micro web site. |
|
What is Spydawn and should I install it? According to Wikipedia, "Spydawn is a malware program that claims to be a commercial anti-spyware, when in fact it is, itself, adware-advertised. The software installs itself, without consent, in user's computers and registry. It then sends messages such as "System Error, Buy this software to fix" or "Your System is infected with spyware, buy Spydawn to clean it", redirecting the user to Spydawn' homepage where he/she is prompted to buy the Spydawn software." Should you install Spydawn if you get a pop-up saying your machine is infected? ABSOLUTELY NOT! For the nominal charge of $39.99 you will have had the pleasure of further infecting your machine, which will require hours of clean-up and could result in a possilbe loss of valuable data if you do. What can I do if I am infected with Spydawn? At On-Site our technicians are experienced in virus, trojan, adware and spyware removal. We will make every attempt to preserve your data, whether it be your business' QuickBooks™ data or the pictures of the grandchildren from last summer's holiday at Martha's Vineyard. |
|
SpyDawnUpdated: May 31, 2007 5:09:56 PM Type: Other Risk Impact: Medium Systems Affected: Windows 2000, Windows 95, Windows 98, Windows Me, Windows NT, Windows Server 2003, Windows XP BehaviorSpyDawn is a security risk that may give exaggerated reports of threats on the computer. The program then prompts the user to purchase a registered version of the software in order to remove the reported threats.Note: Definitions dated before May 18, 2007 may detect this security risk as VirusBurst. Protection
|
|
|
What is SmitFraud? SmitFraud is a type of spyware that installs itself into a computer via adware, without any notice from the user. It can affect all Windows platforms made between 1995 and 2003.[citation needed] Most of the time, it installs itself after the computer user installs a fake codec, such as BrainCodec, PCodec or VideoKeyCodec.[citation needed] It infects a Windows DLL with a computer virus.[citation needed] SmitFraud changes the infected computer's desktop background either into a Blue Screen of Death, or any background displaying a fake error message. Infected users also receive notifications asking users to install a fake anti-spyware program such as SpySheriff, SpyAxe or Spyware Quake, on the infected computer to remove the spyware. After a fake scan, the program asks users to pay for the full version before removing the spyware it's found. When users pay, the notifications disappear and the background turns normal, but the infection is still present. Read the entire article at Wikipedia. |
|
|
Symantec/Norton - www.symantec.com |
Trend Micro - www.trendmicro.com |
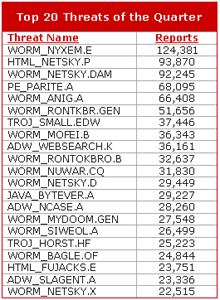 Worms - The Top 20 List
Worms - The Top 20 List